Have you anytime expected to make solid areas for for your PC; email or other kind of record, but it was hard preparing an idea or it was difficult to recall that it the going with decides will help with that. They cover the guidelines or necessities to make solid areas for an and a model on the most ideal way to make one Secret notes should not have your name, last name or other individual nuances associated with you. I grasp that it might be hard all along yet with time it will end up being straightforward. Secret notes should be changed reliably, the environment At times it’s a must changing a mystery expression at standard stretches; with the exception of assuming that it’s a blend of a PIN with a SecurID Token/RSA.
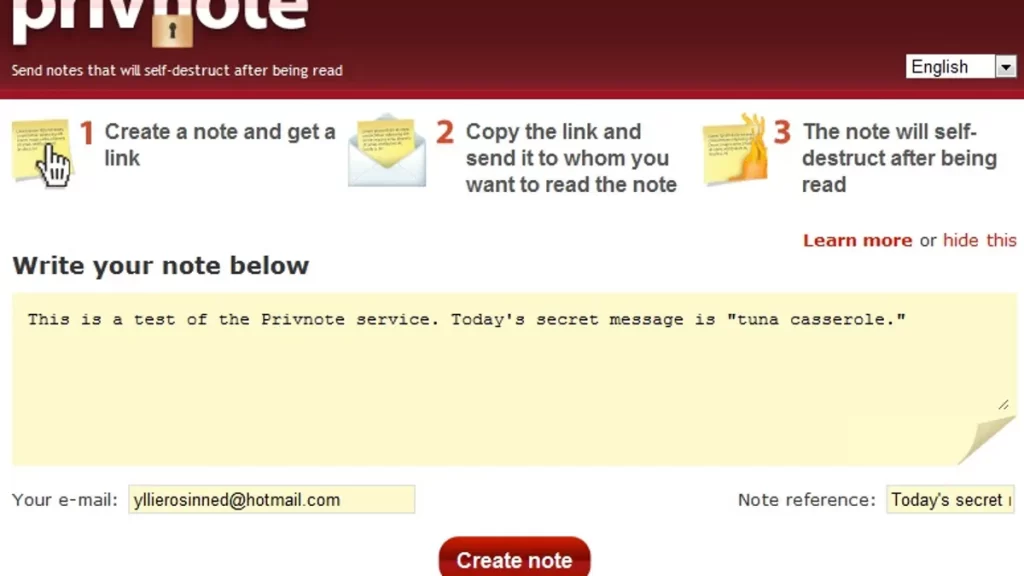
Accepting you resemble me that suggest that you moreover contributed energy with the PC. We should expect that you will for the most part get online at 7PM and that you contributed an ordinary energy of 2hrs on the PC. As of now let’s join every one of the information as one we will include explicit words or letters to make a Secret notes. As you can see I used 2 numbers, added a picture which I made it to be and move 7 and I formed night with promoted N. The Secret notes agree to the standards yet it might be to some degree more grounded. That ought to be conceivable by separating Night so rather privnote making the Secret notes privnote making more grounded. The clarification is that completed words are weaker against word reference and savage power attacks. Another assortment to the Secret notes can add where in the circumstance.
Without vulnerability, web working with is a must-learn point for each progressed business person nowadays. Since you are examining this article, there is a high opportunity that you are truly looking for the right web have You should never reveal your Secret notes to others with the exception of in the event that you would not worry the way that the other individual methodologies that information. Expecting you really want to screen your Secret notes, you truly ought to store them in a manner that is safeguarded from the full fixations eyes of anticipated interlopers. The rule is to keep them in a space that is away from the PC and where they are not successfully gotten to.
You may also like
-
Buying Discord Members Can Kickstart Your Community’s Engagement
-
Unleash the Potential of Videos Quick AI Summarization for Smart Learners
-
The AI Revolution in Excel – How Machine Learning is Elevating Spreadsheet Capabilities
-
Safeguard Your Data from Hackers with Our VPN
-
Wallpaper Plan any Significant Focuses to wishes